SMS scams have really found themselves in the news lately. The mainstream media has publicised the problems a lot. Whilst there are indeed some threats out there and bad actors, what you’ve got to keep in the back of your mind at all times is that the majority of Business SMS transactions (numbering over 2 trillion – yes, TRILLION – annually) are genuine and get delivered without issue. No communications channel is perfect though. And the Business Messaging market is growing fast. Very fast. COVID-19 has accelerated this yet further.
The problem is that a huge growing market becomes an even more attractive place for bad actors to do their stuff. So called ‘phishing’ messages (attempts to unwittingly trap people into giving out personal information that can be used for financial gain and other reasons) are really on the up. Another known (but less common) issue is the so-called SIM swap, when a duplicate SIM card is issued to gain access to an account using false information/forged documents. More often than not, these fraud types are aimed at regular mobile subscribers like you and I. But enterprises are not left out from all these fun and games.
Enterprises can all too easily become victims of scammers and in this article, we’d like to highlight just some of the cases Intis Telecom have encountered along the way.
Intis Telecom has been providing SMS notification services for over 12 years, and throughout this period, both the Russian (our home one) and global markets have been growing steadily. In 2020, the global SMS market amounted to more than $ 40 billion, of which about $ 2 billion is the Russian market. These amounts are not small, and for some SMS aggregators the temptation to use fraudulent schemes and simply steal customers’ money is just too strong. And steal they do.
First, a little background. Business SMS can be roughly split into two different types: transactional and marketing.
Transactional related SMS is the area principally fuelling this massive growth in messaging. Think appointment confirmations, two-factor authentications for online financial transactions or logging into an application, delivery confirmations etc. The list of use cases is practically endless. With these types of transaction people are really expecting to receive this valuable content rapidly. They’re important. Marketing messages are not exactly the same.
Sure, we all like receiving content with special offers on products and services we actually like and use but it’s rarely the case where we find ourselves sitting there looking at our phones waiting for the offers to pop up. If they don’t arrive, most of us will think little or nothing of it.
Until 2014, the default operator commercial model for SMS was charging for delivered SMS only, which had both advantages and disadvantages. Currently, mobile operators charge for all submitted SMS so whether a message gets to the destination or not (whatever the reason for failure – message sent to a non-existent number etc.), the sender is charged.
So that’s the commercial side of things in play across much of the world, let’s get down to the details of the two main fraud types we have seen time and again:
- Blatant fraud – charging for messages destined for inactive/invalid numbers without even attempting delivery!
- Artificial traffic generation on the client side e.g., fake account registrations
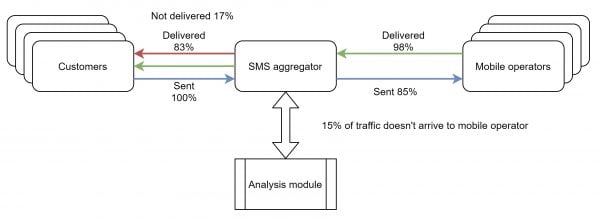
Here’s how the first scheme works:
As the enterprise client pays for all SMS, whether delivered or not, the SMS aggregator analyses the traffic and estimates the likelihood that the number is inactive. They can do this based on previous messaging campaigns or simply by exchanging similar data with other SMS aggregators. The message is tagged with the status ‘undelivered’ but the client is none the wiser and still pays for it. The aggregator cashes in receiving 100% of the profit as the message didn’t even reach the mobile operator to be relayed to the final destination.
Depending on how neglected an enterprise client’s database may be, the bad aggregator’s profit can reach 15-20% of their total business with the client. That really adds up.
So how are customers trying to combat this out-and-out scam? Well, firstly, they may have a defined list of test numbers to which they periodically send SMS to. The effectiveness of this method is rather low though because the test numbers’ usage patterns tend to differ greatly from the traffic profile of a real subscriber. It’s not difficult for the SMS aggregator to find them and white list them, ensuring test messages are accorded the highest priority and routed rapidly via the most direct route possible.
Another way of detecting and combating this type of fraud is for the client to request summary data from mobile operator, for example how many SMS transactions were sent to the operator for the reporting month with their company sender ID. They then compare it with their own traffic records. In the event of a noticeable discrepancy, they file a complaint with their SMS provider. This method tends to be available to only the larger clients though – banks, government institutions and the like
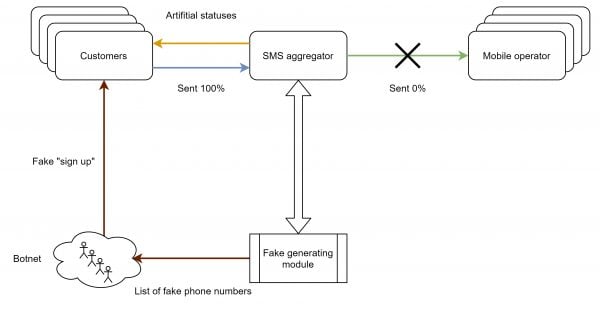
The second fraud scheme (artificial traffic generations) is more sophisticated, but also more profitable. Here’s a diagram explaining how the scam works:
Let’s say a customer has an online store where users register and make purchases. How is SMS usually used in this business process?
- An SMS is sent during registration process to verify your phone number – part of KYC, knowing your customer, verifying people are who they say they are
- Order status notification;
- Forgotten password recovery;
- SMS when logging on – 2FA, two-factor authentication.
So, the SMS aggregator generates a number range for the operator of interest. Usually, the most expensive one is chosen but other operators may be mixed in to make the fraud less conspicuous. The number range is transmitted to the botnet, which performs actions in the store leading to the sending of SMS. The client naturally sends these SMS messages to the aggregator and they in turn generate fake statuses for the client whilst simultaneously transmitting the data contained in the text (for example a one-time code, password, etc.) to the botnet to complete the automatic operation.
The net result is that the online store is left with a number of dead registrations and an inflated SMS bill, all whilst the SMS aggregator pockets the full cost of the message.
The scam has a more direct variation in the form of crude, deliberate generation of artificial traffic. It is used to discredit competitors. Decent aggregators are made to look bad in the eyes of their client enterprise. The bad aggregators then miraculously approach the client enterprise at the same time, selling themselves as THE trusted aggregator to do business with. The enterprise client switches to the new aggregator who they THINK is reliable and honest but it far from it. Quite the opposite in fact. The classic strategy of creating a problem on one side, only to propose a solution on the other.
And here we now have to ask ourselves the two classic questions: “Who is to blame?” and “What can be done?” Strangely enough, the enterprise clients ultimately only have themselves to blame most of the time.
Firstly, when it comes to an enterprise putting their Business Messaging out to tender, price is too frequently the only real factor they consider. They take the lowest price offered, an unsustainable price no honest aggregator could ever work with without losing money from the start. They’re left with an aggregator who resorts to pulling every trick they know to maximise profit and make the rate work for them. The enterprise’s customers’ experience suffers and the enterprise risks serious reputational damage.
Secondly, enterprises that really do not help themselves by having client databases with truly poor data accuracy and integrity.
So now to the “What can be done?” part. We’ve been in business for so many years and can recommend the following ways to combat fraud:
- Periodically ‘clean’ your customer database, ensuring numbers which no longer exist are removed as well as of course data for people who are no longer your client. Keep in mind that either you or your Business SMS supplier could do this but either way, any enterprise that really stays on top of their client database integrity will save money.
- Always aim to achieve a high successful delivery rate (SDR) for all the SMS traffic you generate. A typical, good delivery percentage for SMS campaigns (marketing) runs in the 90-95% range and for SMS transactional notifications, 97-99%.
- Conduct an audit of your IT infrastructure, applications, online stores etc. in order to prevent automatic actions from being allowed. Even the simple addition of Google ReCaptcha (including invisible) will significantly complicate the automatic actions of any botnet a bad actor looks to employ
- Monitor metrics (volumes, successful delivery percentages, distribution of the share between operators) and, in the event of a sharp change in any indicator, conduct an investigation and ask questions of your supplier.
- Do not hush up the identified cases of fraud and make them public to the widest possible extent. As long as you have concrete information to back up any allegation, naming and shaming is really the only way to clear the market of unscrupulous players. Of course, regulation and enforcement by authorities plays a role too but this route can take a long time to deliver the required result.
We hope you’ve found our article enlightening. There are way more than just two SMS fraud types out there but the two mentioned are ones we see coming up time and again right now. Thanks for reading and if you are looking for a Business Messaging company that knows what they are doing, is honest and protects your business and customers, then look no further than Intis Telecom!